Table of Contents
- What is SKI Decryption?
- How Does SKI Work?
- How does SKI re-enable Decryption for Passive Systems?
- How does SKI activate Decryption for Inline Systems?
Nubeva SKI for TLS/SSL Decryption
Nubeva's SKI for TLS is a software system that provides efficient decryption of all TLS and SSL traffic, including TLS 1.3, 1.2 with PFS, pinned certificates, and mutual authentication sessions. It is designed to serve both passive and inline applications, addressing the deficiencies of traditional decryption methods and enabling thorough packet inspection in modern environments.
The emergence of TLS 1.3 and the increased use of PFS with TLS 1.2 have made passive decryption of TLS traffic ineffective, leaving inline systems as the remaining solution. However, forward and reverse proxies introduce latency, create costly bottlenecks, disrupt open sessions, and often fail with pinned or mutually authenticated sessions, thereby affecting security, privacy, and scalability. This has led to organizations inspecting less of their data in transit, increasing difficulty in identifying malicious activity hidden in regular traffic patterns and potentially facilitating ransomware and data exfiltration.
Nubeva's SKI for TLS presents a comprehensive solution to these challenges. We offer a toolkit comprised of various software components available in both binary and source code options. This toolkit is designed to facilitate the construction or enhancement of both passive and inline decryption systems SecOps, DevOps, Integrators, and OEMs. With SKI, organizations can effectively navigate the complexities of modern traffic decryption, bolstering the security and efficiency of their systems.
What is SKI (Session Key Intercept)?
Nubeva SKI is a powerful, new approach to decrypt modern TLS (SSL) traffic. With the advancements in today’s application, computing, and networking environments, SKI delivers a leap forward in capability and performance to quickly enable cybersecurity and application monitoring systems. SKI is employed both as an augmentation to legacy forward and reverse-proxy engines or as a fix to passive intercept systems due to pending obsolescence from Perfect Forward Secrecy.
Nubeva SKI Delivers:
The Decryption of Any TLS for Passive and Inline systems
- TLS 1.3, 1.2 with PFS, and legacy 1.2, 1.1, 1.0
- TLS 1.3 handshakes
- Pinned Certificates
- MTLS/Client Certificates
- Traffic to foreign/3rd Parties internet and cloud services
- Encrypted SNI (eSNI) and TLS 1.3 Handshakes
For Any Environment and Traffic Flow
- Metal, VM’s, Containers, Kubernetes, and microservice architectures (including Services Mesh Architectures)
- Datacenter, Cloud, Hybrid
- Servers, Clients, IOT
- Inbound, outbound, and east-west sessions
How Does Session Key Intercept (SKI) Work?
SKI provides the ability to GET SESSION KEYS from TLS clients and servers in real-time and to USE SESSION KEYS to decrypt TLS on authorized systems to enable deep packet inspection.
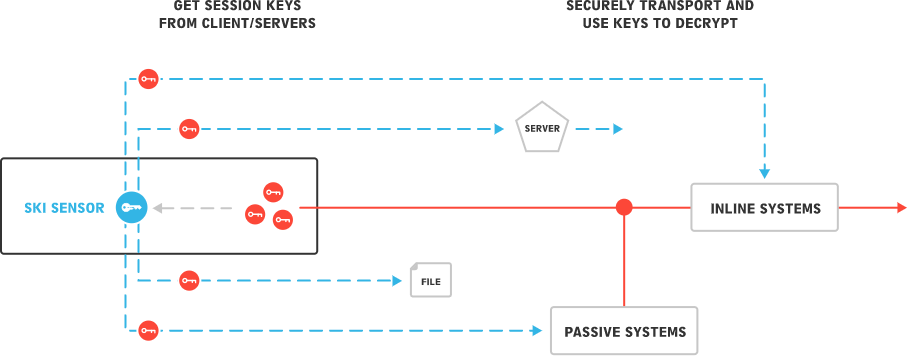
With session keys available, one can decrypt any session with simple and efficient bulk decryption. As such, SKI is universal to all traffic flows and use cases and applications: inbound, outbound, east-west, clients, servers, data center, cloud. Since TLS session keys are symmetric (shared by both endpoints), keys only need to be obtained from one side of a connection and therefore can apply to client connections to foreign servers and services.
The idea of getting and using keys is not a completely new concept. Keylogging, typically used by DevOps/SecOps and in some commercial systems has been widely used for a long time but is not a viable solution for scaled and secure mission-critical use. With SKI, Nubeva has taken the basic idea of keylogging and delivered an enterprise-grade, complete solution for modern TLS visibility.
Unlike legacy man-in-the-middle/forward proxy, session pre-termination/reverse proxy, and RSA Passive Intercept, SKI does not involve certificates or server keys, nor does it manipulate or change traffic, connections, authentication, or PKI. Instead, it simply works with the individual TLS session encryption keys (aka, ephemeral, symmetric, or bulk encryption keys) that are developed during the handshake, shared by the TLS client and servers, used for the bulk encryption/decryption of the communication, then discarded.



